Data & Application Security 🗄️ Protect Data. Secure Applications. Build Trust. 🔐
Data powers your business, and applications are the core of your operations. These digital assets are highly targeted by cybercriminals aiming to steal, manipulate, or disrupt sensitive information. Securing data and applications at every stage—from development to deployment to storage—is critical to maintaining business trust, uptime, and compliance.


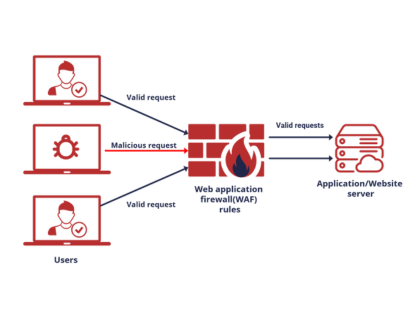
Threat Protection
Application Firewall (WAF), Runtime Application Self-Protection (RASP), and Database Security to defend applications and databases from exploits and attacks.
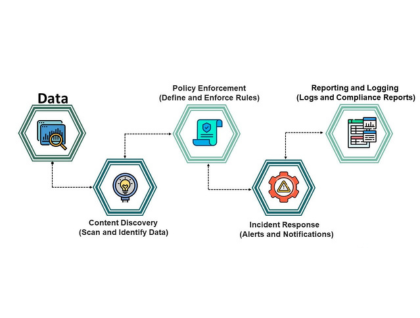
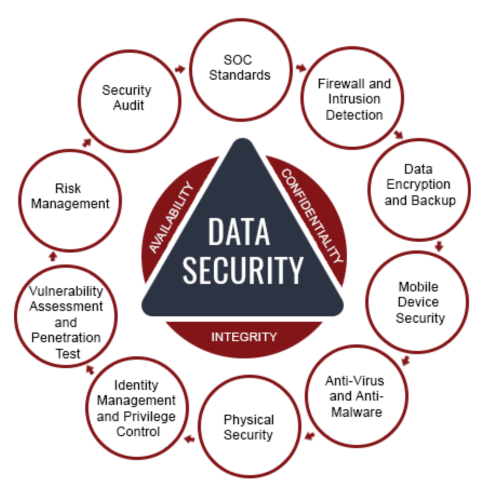
Data Security
Data Encryption, Data Loss Prevention (DLP), and Backup & Disaster Recovery to safeguard business data in storage, transit, and during outages.
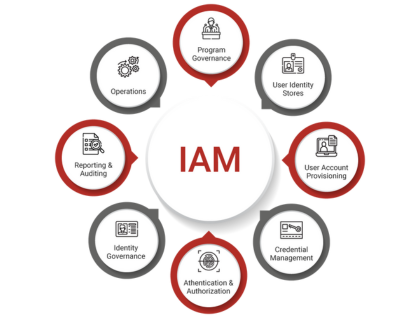
Access & Identity Control
Identity & Access Management (IAM), Multi-Factor Authentication (MFA), and Privileged Access Management (PAM) to control and secure user access.
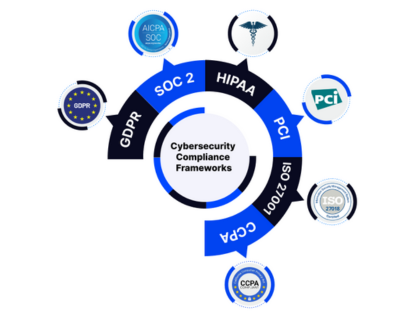
Monitoring & Compliance
Application Security Testing (SAST/DAST), Compliance Management (GDPR, HIPAA, PCI-DSS), and Logging & Threat Analytics to ensure visibility, governance, and regulatory adherence.

HOW WE DO
We don’t just protect files—we secure the entire data journey and application stack with intelligent, layered defense.
Encryption & Access Policies for Critical Data
Continuous App Vulnerability Scanning & Patching
RealTime Threat Detection,Automated Response
Database & API-Level Protection Against Exploits
PRODUCTS WE SUPPORT
We associate with trusted data and application security vendors:



WHY IT MATTERS
Unsecured data and vulnerable applications are leading causes of cyber incidents. Without proper protection::
- Sensitive customer or business data can be leaked or stolen.
- Applications and APIs can be exploited, leading to downtime or financial impact.
- Data corruption or ransomware can halt operations.
- Compliance violations may result in legal penalties and loss of trust.
🗄️ We help organizations build secure, compliant, and resilient data-driven systems—ensuring applications and data stay protected across every layer.
FREQUENTLY ASKED QUESTIONS
What is data & application security?
It’s the protection of sensitive data and applications from unauthorized access, misuse, or cyberattacks.
Do you provide encryption for sensitive business data?
Yes, we secure data at rest, in transit, and in use.
Can you help secure custom-built applications?
Absolutely—we provide vulnerability assessments and ongoing monitoring.
How does DLP work?
DLP policies monitor, detect, and block unauthorized transfers of sensitive data.
Is compliance part of data security?
Yes, we ensure data handling aligns with standards like GDPR, HIPAA, and PCI DSS.

