Identity & Access Management 🔑 Right Access. Right People. Right Time. 🛡️
User identities and access permissions define the security boundary of your organization. Weak authentication, excessive privileges, or compromised credentials can open the door to serious cyber threats. Strong IAM ensures that only the right people access the right resources—at the right time and under the right conditions.

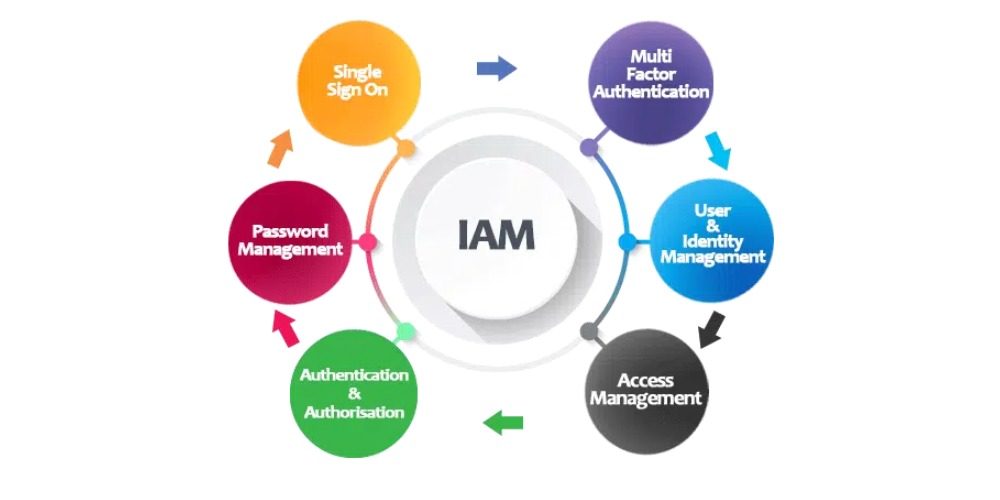
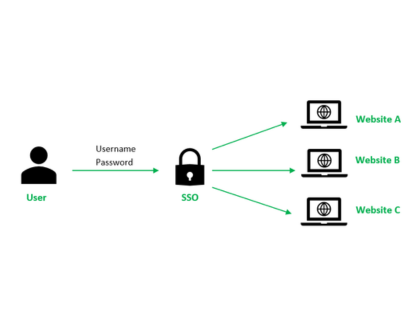
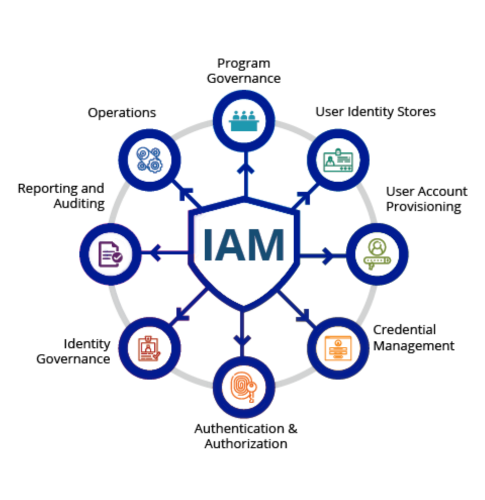
Authentication & Authorization
Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Role-Based Access Control (RBAC) to provide secure and role-based user access.
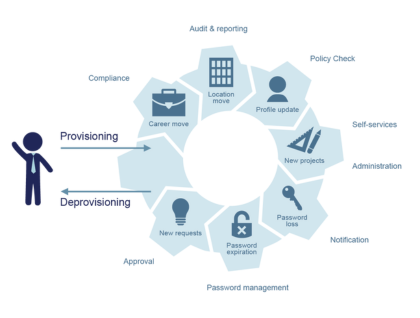
Identity Governance & Administration
User Provisioning & Deprovisioning, Identity Lifecycle Management, and Access Certification & Policy Enforcement to manage identities throughout their lifecycle.
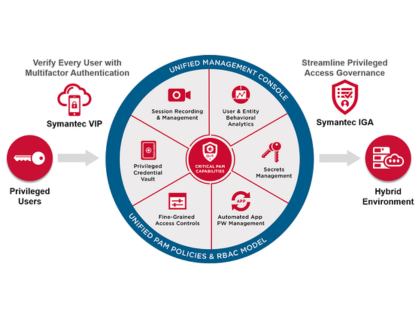
Privileged Access Management (PAM)
Privileged Account Security, Session Monitoring & Recording, and Just-in-Time Access to secure and control high-level user accounts.
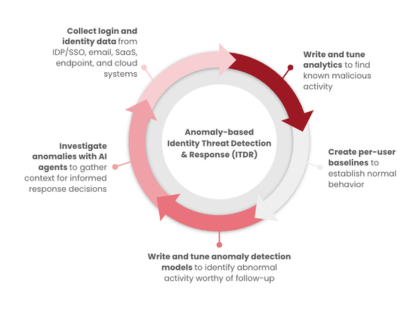
Monitoring & Intelligence
Audit Trails & Reporting, Anomalous Behavior Detection, and Identity Threat Detection & Response (ITDR) to ensure visibility and respond to identity-based threats.

HOW WE DO
We centralize identity control and enforce secure access policies with automation and continuous monitoring:
Enforce Secure Authentication Methods
Automate User Provisioning & Access Rights
Monitor and Block Suspicious Login Attempts
Reduce Insider and Credential-Based Threats
PRODUCTS WE SUPPORT
We associate with leading IAM platforms:






WHY IT MATTERS
Identity misuse is one of the most common causes of cyber breaches. Without strong identity and access control:
- Attackers can exploit stolen or weak credentials.
- Employees may gain unauthorized access to sensitive systems.
- Insider threats become difficult to trace.
- Compliance and audit requirements may fail.
🔑 We assist organizations in securing digital identities and enforcing least-privilege access—building a safer and more controlled IT environment.
FREQUENTLY ASKED QUESTIONS
What is IAM?
IAM (Identity & Access Management) is a security framework that manages user identities and controls who can access which systems and resources within an organization.
Do I need IAM if I already use strong passwords?
Yes. Passwords alone are not enough—IAM adds layered security with MFA, access control policies, and monitoring to prevent unauthorized access even if credentials are compromised.
Can IAM support remote and hybrid teams?
Absolutely. IAM enables secure access from any location by enforcing authentication policies, monitoring access behavior, and ensuring users only access approved resources.
Do you integrate IAM with existing systems and tools?
Yes. IAM solutions can be integrated with your current applications, VPN, email services, cloud platforms, and directory services like Active Directory or Azure AD.
How does IAM support compliance and audit readiness?
IAM helps meet compliance by maintaining detailed access logs, enforcing least-privilege policies, and generating audit-ready reports required by standards like GDPR, ISO, PCI-DSS, and HIPAA.

