Vulnerability Assessment & Penetration Testing 🕵️ Find Weaknesses. Fix Gaps. Stay Secure. 🔐
Cyber attackers constantly look for gaps in systems, networks, and applications. VAPT helps organizations identify vulnerabilities before they are exploited. By simulating real-world attacks and providing actionable remediation, VAPT strengthens the overall security posture of your business.

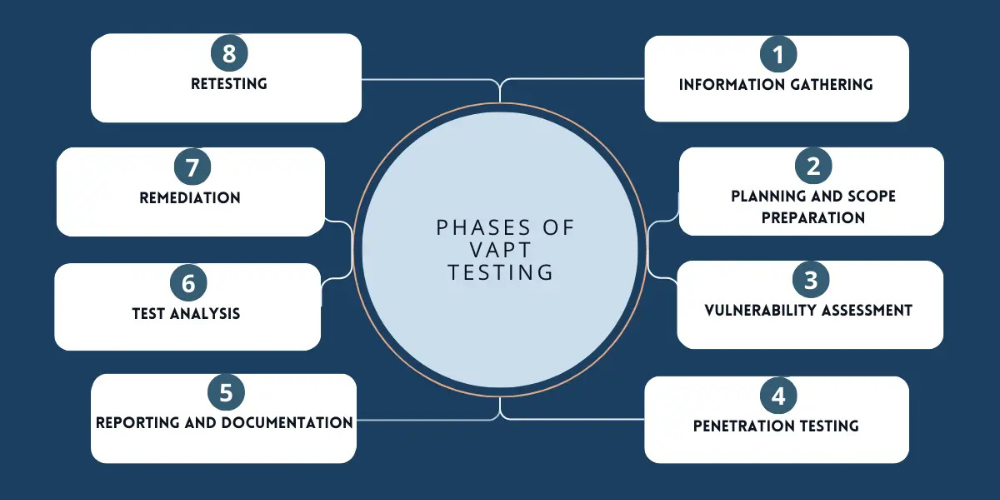
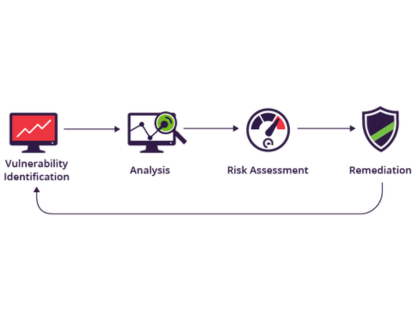
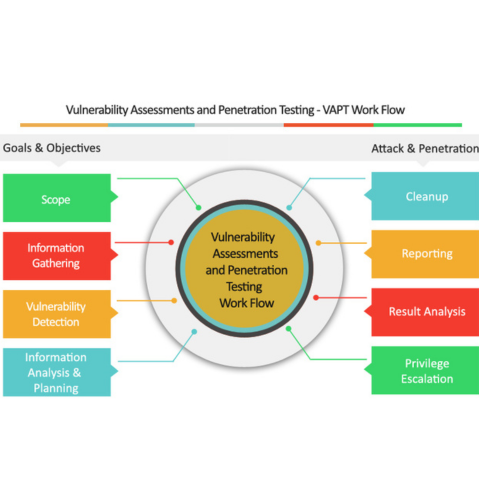
Vulnerability Assessment
Automated Scanning, Configuration Review, and Patch & Risk Prioritization to identify and prioritize security weaknesses across systems.
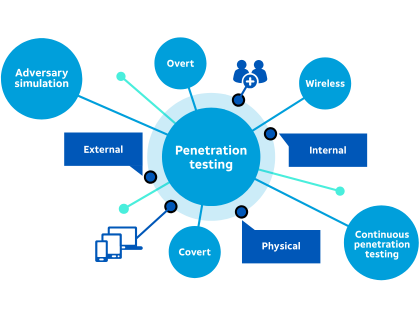
Penetration Testing
Network Penetration Testing, Web & Mobile Application Testing, and Wireless & Cloud Pen Testing to simulate attacks and uncover exploitable flaws.
Security Controls Testing
Social Engineering Testing, Physical Security Testing, and Security Configuration & Hardening Validation to assess defenses and employee awareness.

Reporting & Continuous Improvement
Detailed Risk Reports, Remediation Guidance, and Continuous Testing & Compliance Support to provide insights, fixes, and ongoing security alignment.

HOW WE DO
We combine automated tools with expert-led testing to provide a comprehensive security assessment:
Continuous vulnerability scanning and monitoring
Risk scoring and prioritization to focus on critical issues
Detailed reports with actionable remediation steps
Retesting to verify fixes and improvements
PRODUCTS WE SUPPORT
We associate with leading VAPT tools and frameworks:






WHY IT MATTERS
Undetected vulnerabilities are open doors for cybercriminals. Without VAPT:
- Hackers can exploit unpatched systems
- Web apps and APIs may leak sensitive data
- Cloud misconfigurations can be abused
- Compliance requirements may not be met (PCI DSS, ISO, GDPR)
🕵️ At Amlak, we assist businesses in finding and fixing security gaps before attackers can exploit them—building resilience and trust.
FREQUENTLY ASKED QUESTIONS
What is the difference between VA and PT?
VA finds and reports weaknesses; PT tests if those weaknesses can actually be exploited.
How often should VAPT be performed?
At least annually, or after major changes in systems or applications.
Do you provide detailed reports?
Yes, we deliver risk-based reports with clear remediation steps.
Can you test cloud and APIs?
Yes, we include cloud platforms, APIs, and SaaS apps in our testing.
Is VAPT required for compliance?
Yes, many standards like PCI DSS and ISO mandate regular security testing.

